
Confidential information is any data that could be used to harm an individual or organization if accessed by someone with ill intent. The data can take many forms from financial information to product plans to customer lists. Businesses should set up strict policies and procedures to ensure they are protecting confidential information and prevent unauthorized access.
An effective information security plan can provide clear guidelines on how your organization will safely handle data. Data breach prevention builds trust with the public and maintains legal compliance with privacy regulations.
Types of Confidential Information
Confidential information comes in many forms. It may be kept on physical documents, stored electronically, or even passed through oral communication. Generally, confidential information in the workplace can be divided into four categories:
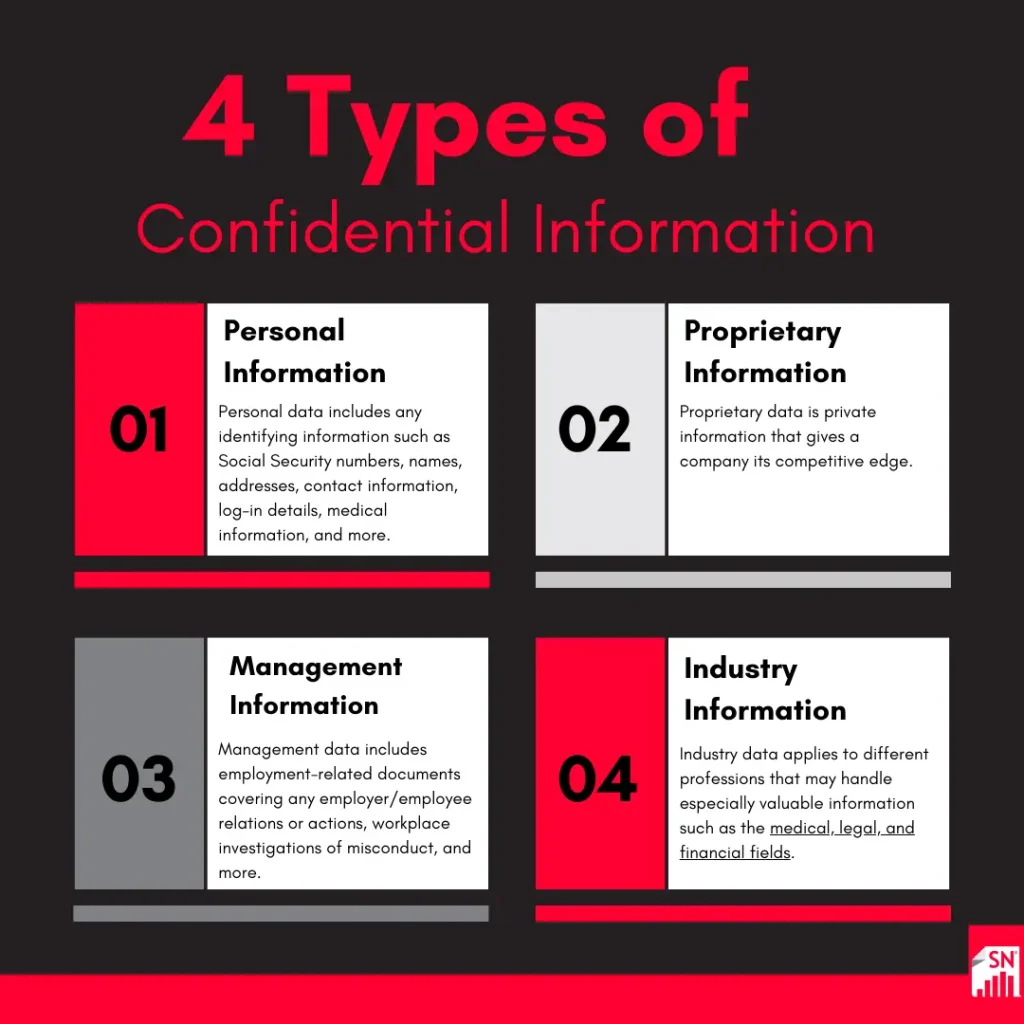
- Personal Information: Personal data includes any identifying information such as Social Security numbers, names, addresses, contact information, log-in details, medical information, and more. Businesses store personal information for both employees and customers. They are responsible for properly handling this data to prevent identity theft and fraud for these individuals.
- Proprietary Information: Proprietary data is private information that gives a company its competitive edge. It includes information like customer lists, suppliers, pricing strategies, commercial processes, product development, trade secrets, budgets, forecasts, and more. This kind of data is generally protected by contractual agreements between the parties involved.
- Management Information: Management data includes employment-related documents covering any employer/employee relations or actions, workplace investigations of misconduct, salary and contract negotiations, planned layoffs, and more.
- Industry Information: Industry data applies to different professions that may handle especially valuable information such as the medical, legal, and financial fields. Records containing medical diagnoses and treatments, tax information, and privileged communications require extra protection.
Breaches of Confidentiality
Threats to private information can come from both inside and outside of your business. Leaks can be intentional through theft, hacking, and corporate espionage or unintentional through disorganization, loss of documents, and lack of safe business transactions. Failure in protecting confidential information can be very damaging to any organization.
When data is mishandled your reputation is at stake. Customers and clients will lose trust in your business, hurting your bottom line. If employee information is exposed, you may lose the trust, morale, and loyalty of your team. You may face huge non-compliance consequences and risk exposure of the intellectual property that gives your business its edge.
How to Protect Confidential Information
Below is a list of business practices to maintain confidentiality in the workplace.
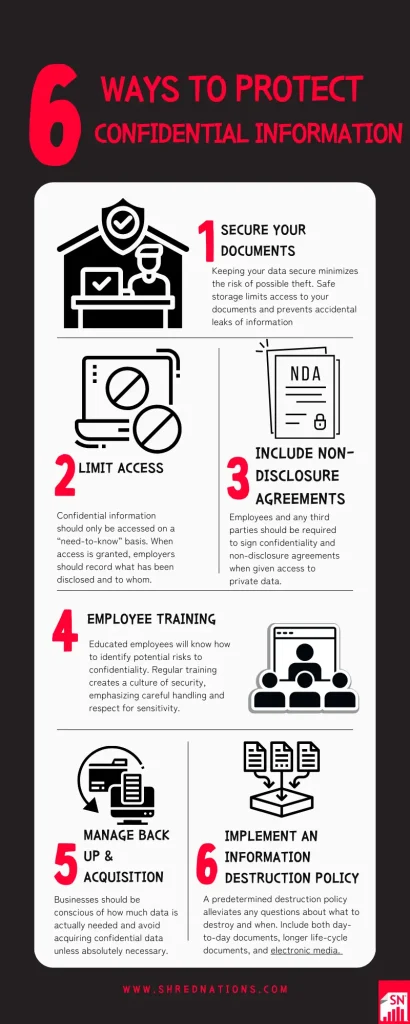
Secure Your Documents
Keeping your data secure minimizes the risk of possible theft. Safe storage limits access to your documents and prevents accidental leaks of information. Active documents should be locked and monitored whether they are physical or electronic. Documents with extended retention periods should be kept in offsite storage for professional management and security.
Limit Access
Confidential information should only be accessed on a “need-to-know” basis. When access is granted, employers should record what has been disclosed and to whom. Permissions should be revoked once a project is complete or no longer appropriate. Electronic data should always be password-protected and encrypted.
- Implementing a strict visitor policy should also be implemented where appropriate. Visitors should sign a confidentiality agreement, be escorted at all times, and be kept away from areas where they may be exposed to sensitive data.
Include Non-Disclosure Agreements
Employees and any third parties should be required to sign confidentiality and non-disclosure agreements when given access to private data. This protects your business from leaks of information and can prevent legal issues down the line.
Employee Training
Educated employees will know how to identify potential risks to confidentiality. Regular training creates a culture of security, emphasizing careful handling and respect for sensitivity. Specific training should be provided for:
- Safe handling of electronic and physical documents, covering the entire life cycle of information.
- A clean desk policy to maintain clear workspaces at the end of each day, including locking up files, documents, electronic media, and USB devices.
- A digital device policy to follow basic cybersecurity measures including anti-virus software, firewalls, encryptions, whitelisting applications, and routinely patching software.
Manage Back Up & Acquisition
Businesses should be conscious of how much data is actually needed and avoid acquiring confidential data unless absolutely necessary. Reducing the amount of data you are handling, reduces risk. Back up important documents in case of loss, theft, or damage to maintain access even if the worst does happen.
Implement an Information Destruction Policy
A predetermined destruction policy alleviates any questions about what to destroy and when. Include both day-to-day documents, longer life-cycle documents, and electronic media.
- A shred-all policy means all documents are shredded and placed in secure shred bins. This takes away human error in deciphering what should be shredded and reduces the risk of a breach.
- Documents with extended retention rules should be stored safely and indexed by the destruction date. When the retention period has passed, documents should be destroyed in a timely manner.
Shred Nations is an Industry Leader in Protecting Confidential Information
Shred Nations offers secure storage and shredding services to protect your business. Call us at (800) 747-3365 to fill out the form to find services near you. We will instantly connect you with multiple providers and send you free quotes on the services you need. We look forward to protecting your confidentiality with our reliable options.













